For this week’s exercise, we were assigned the following three pieces of information to search for on the Internet:
- An op-ed on a labor dispute involving public school teachers from before 1970
- The first documented use of solar power in the United States
- The best resource for the history of California ballot initiatives, including voting data
To say the very least, this assignment definitely put my searching skills to the test, and even resulted in changing the way in which I search for material. Below is the journey of how I attempted to find those items, and the tools that helped me achieve success (or at least extremely close second guesses).

Image taken from http://marketingmatters.dexone.com
Exhibit One: Labor Disputes involving Public School Teachers, circa 1970
While I normally would have gone straight to Google, my go to search engine in times of need, this exercise stretched me to think more…outside the box. Putting on my detective hat for a few minutes, I thought about what other sources available to me online would help me get closer to finding the answer. Realizing that this information, as an op-ed, would be in a newspaper or magazine, I chose to go straight to ProQuest, specifically the historical newspaper database we had used in class earlier this week. Once I had pulled that page up, I used a few various keywords to limit my search, including: labor, dispute, public, and teacher. ProQuest came up with a long list of articles and newspapers that held a few of those keywords that I had selected, but i quickly found out that they didn’t fit the time specified in the assignment or the placement in the newspaper itself, specifically opposite the editorial page. After perusing the site a bit more, I found the ‘sort results by’ box, where I could narrow down my search results by a number of different characteristics. So, I narrowed down the timeframe, blocking out articles published before 1970, as well as the type of document that would be displayed, including editorial and commentary. After plugging these requirements into my new search, I quickly came up with a number of articles that fit what I was looking for, one of which is displayed here. Overall, once I changed the way in which I approached searching the item, this topic became one of the easiest to find.
Exhibit Two: First Documented Solar Power Use in the U.S.
In contrast, this item was much harder to find than the first, and to be honest, I’m still not sure I have the right answer (although I’m sure I’ll figure out the right answer tomorrow). Again, I tried to use the process of reasoning to figure out which techniques would be the most useful in helping me find this gem of a search subject. At first, I thought through what types of webpages or sites would hold the information I wanted. After thinking for a few moments, I figured environmental sites would be one of the first that I should check. While I had initially thought of government sites, specifically the Department of Energy or even NASA, I wasn’t sure that wouldn’t just lead to more deadends than it would unturn. So, with that in mind I searched Google not using the keywords of solar energy and documented uses, but I searched for webpages that had the history of enviornmental science of the United States. I had a number of results come up, some more scholarly than others. After browsing through a few of the 105 million results Google came up with, I decided to try the webpage from the University of Radford, conventiently the first page that was listed. Once I got to the main page, I re-evaluated the data that I needed to find, namely solar power in the United States and the earliest documented use. On the main page, there was a timeline at the top of the page, as well as a ‘special features’ side tab that broke down the site into various categories. Instead of going decade by decade, I decided to use the special features tab first, clicking on ‘fuel of the future’ as my first avenue of searching. While I thought this would include various types of powering of vehicles and devices, I quickly found that this was not the case. Rather, the page focused on the use of ethanol as fuel. Having used up that option, and not seeing any of the other categories as relevant, I chose to go through the timeline by decade, starting with the latest available. After searching through a number of decades, I finally found my answer: Baltimore inventor Clarence Kemp, also known as the “father of solar energy in the U.S”, patented the first Climax Solar Water Heater in 1891. While this was definitely not the method I would have preferred to have used to find my answer, it worked well and was relatively efficient, more so in my opinion than it would have been had I simply typed the search words into Google.
Exhibit Three: History of California Ballot Initiative
Next to the solar power search, this was one of the hardest to find. Again, I used the logic of thinking through what my search topic was essentially. After determining that a site holding historical data and articles would be the best choice, I decided to use JSTOR. A site composed of journals, I searched through the site by looking at all of the listed journals and periodicals alphabetically. Once I had found the journals focused specifically on California, I used the search tool to look within these journals for the information I needed, specifically ballot initiatives. making sure to include the voter data information by inserting ‘+’ before it. By limiting my search, I narrowed down my search field from 215 entries to 74, finding the most comprehensive article at #44, titled “Constituency Preferences: California Ballot Propositions, 1974-1990”. Out of all of the potential journals and articles that were listed, I chose this specific one due mainly to the expanse of time that was covered concerning the topic (which I felt would give me a better overall feel of any trends in data).
Overall, I have enjoyed this exercise the most out of the ones that have been done so far in this course (granted, its only week three) because of the way it forced me to think outside of the box. Normally, I would have gone straight to Google to find all of these things, and would have been left frustrated or satisfied with the wrong answers. I’m excited to take this new way of thinking and searching to my other classes, especially those focused on historical research.
 This week’s reading, or rather exploration, of Will Thomas’s and Edward Ayer’s historical site, The Difference Slavery Made, was an excellent example of digitizing history in a way that is accessible and informative to a wide array of audiences.
This week’s reading, or rather exploration, of Will Thomas’s and Edward Ayer’s historical site, The Difference Slavery Made, was an excellent example of digitizing history in a way that is accessible and informative to a wide array of audiences. Sections of data in the image above are organized based on the topic they include
Sections of data in the image above are organized based on the topic they include![]()
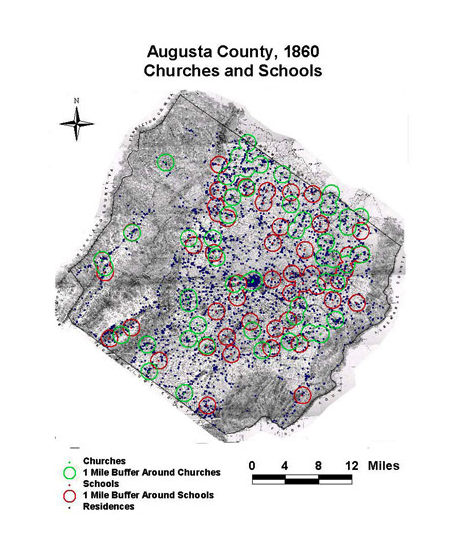 As shown in the map above, the data incorporated on this site usually includes multiple points of analysis and covers topics that I would not have even thought relevant to the topic of slavery, such as soil type.
As shown in the map above, the data incorporated on this site usually includes multiple points of analysis and covers topics that I would not have even thought relevant to the topic of slavery, such as soil type.